Are You Prepared for Next-Gen Phishing Threats?
Phishing is no longer some email scams warning you about account dues and foreign princes. Today's threat actors leverage deepfake, advanced detection evasion mechanisms and extensive research to attack you.

I hate to admit it: I was caught once by my company's phishing simulation campaign. I was late to pick up my kids, I knew my password was expiring, I entered my credentials. And the rest is history.
This is the best proof that people don't fall for phishing because of ignorance. I am in the 0.01% of the population that is the most educated about phishing emails. Still got caught.
No "awareness training" will ever defeat cognitive load and fatigue.
If anyone says otherwise, they're selling something.
Feeling down yet? How about I tell you that things are about to get much worse?
Here's an inconvenient truth: there is an arms race going on between messaging systems security and scammers. Here are the weapons that cybercriminals are bringing to the table.
Deepfakes
Imagine your CEO sending you a voice message telling you to really give access now to his assistant to the company database for a big transaction. The voice is identical thanks to a voice generator such as Eleven Labs. You can even make his face. I made this portrait of Elon Musk in 5 minutes in MidJourney.
That's not even looking at the shady companies that do not filter their AI outputs.
The deepfake problem has become so big that the FBI is panicking, the NSA is issuing 18-page warnings, and the House of Representatives is passing bi-partisan Bills to fight them.
We've seen deepfakes used in Spain to "unclothe" girls, conduct sextorsion schemes, create false advertisement, and voice impersonation to gain access to IT systems.
All you need is a few images on social media!
Today's phishing scams are rudimentary. How can our current filters, which struggle with text-based scams, spot a deepfake before it lands in your inbox?
Alright here's the one I made of myself using only images that are publicly available online:
OK. I admit I may have tried to make myself look more attractive.
So what happens once the deepfake has successfully impersonated someone?
Business E-mail Compromise (BEC)
What is business email compromise? Get ready to get bombarded about this in the next few years. The reason? Verizon's Data Breach Investigation Report (DBIR) identified a 2x spike in such attacks in the past year. BEC is now the dominant technique hackers use in a social engineering setting.
Why? You are much more likely to fall for fraud if the sender is known. Here's a common scenario. I send an email blast to millions of addresses with a simple credential harvester. This is the cheapest attack. But even if you only get 1:100,000 people, that's more than enough to get lucky. In the past, criminals would jump the gun quite quickly. They would try to gain access to the person's workstation and to the corporate network where their emails were hosted. Today, criminals realize there is more value in knowing their victims.
- Wait this person is an accountant?
- Who are the clients?
- What if I asked them to file a fake tax receipt and cashed it in?
- What if I convinced procurement to authorize an expense for my fake product?
- What if I responded to this email thread?
Earlier generations of attackers sought automation. Only recent threats seem to tailor their strategy. And they are not just impersonating people...
Brand impersonation
In their most recent phishing report, Cloudflare observed over 1,000 brands being impersonated in the past year. 52% of the impersonations focus on 20 of them, with Microsoft being the clear #1.
Criminals simply copy these brand's templated emails. They then craft specially tailored URLs using open redirects from vulnerable websites. Using an open redirect on, for example, microsoft.com, threat actors can make a malicious link look like this:
https://microsoft.com/redirect.php?url=http://attacker.com"But wait, this isn't new!" Indeed, you wise reader. What changes now is the impersonation of popular SaaS vendors such as DocuSign, Google Docs or Office 365. Instead of showing a fake login page, the attackers show a malicious OAuth authorization page. What is that? I'm sure you've seen this before:
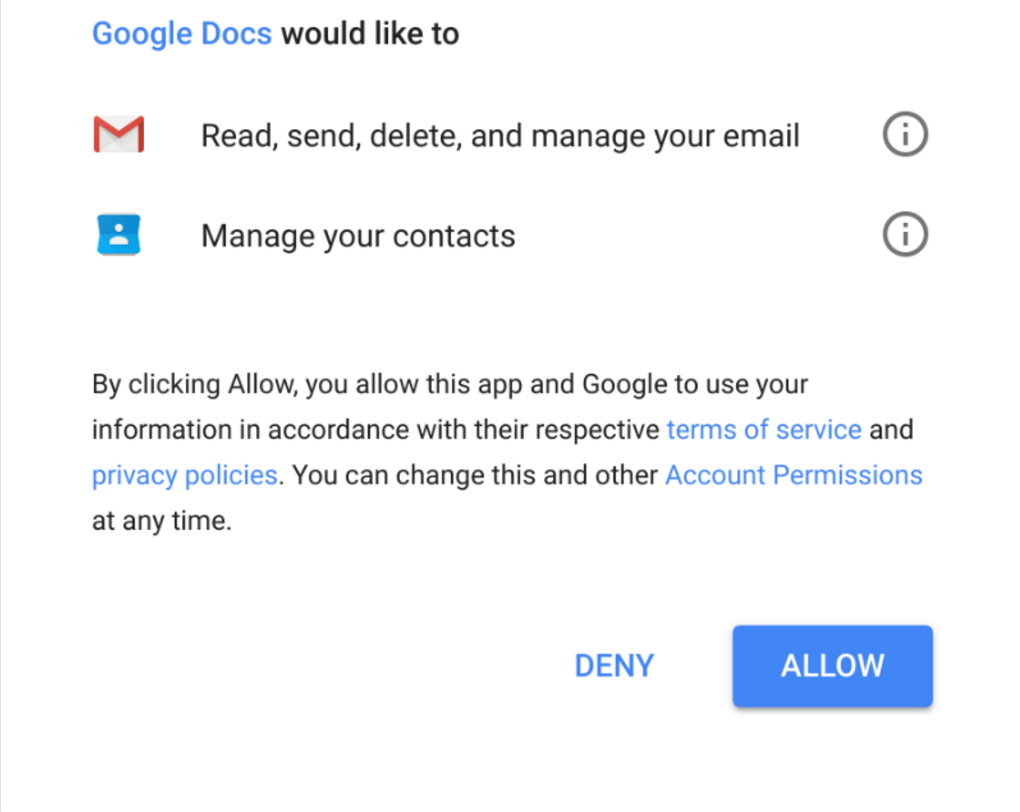
Here, the attackers created a fake app named "Google Docs" which requests the user complete control over their gmail. Thing is, of course, nobody reads what privileges are being requested. So people simply allow the permission delegation and voilà, the attacker now controls your Gmail, with your permission!
So if you think training people about fake login pages does the trick... think again.
Still not scared? How about malicious QR codes, now nicknamed "quishing"? QR codes are images, which can bypass some email protection which are text-based. Yes, email security solutions can do some level of image recognition with machine learning, but this technology is both slow and costly. Generating a QR code, on the other hand, takes milliseconds. Hackers can also use polymorphism to generate variations on QR codes automatically, making them even harder to filter out.
Normally, this is where I recommend to not use email for critical business processes. While my recommendation remains valid, the covid pandemic showed us that attackers could find other ways in...
It's not just emails...
There are many reasons to dislike Microsoft Teams. Windows users can uninstall it all they want, every Windows update keeps bringing it back. The desktop app drains memory. The file system leverages the clunky Sharepoint architecture. And add to that: criminals have Teams misconfigurations figured out.
Teams phishing is now mainstream. Many organizations have chosen to allow other organizations to contact them through Teams. What could go wrong? Threat actors simply have to create a fake Teams tenant to communicate with their victims that have enabled this setting! And voilà, Teams is compromised!
This is a great illustration of the security versus usability tradeoff. Every organization in the world must communicate externally. People will get tired of having IT allow every customer, partner, and prospect in their Teams connections, and the floodgates open to scammers.
In that sense, my recommendation is no longer to avoid emails. It's multi-factor validation for any critical transaction. You shouldn't authorize any payment above $10K without a supplemental communication channel approval, etc.
And remember if you see any deepfakes of myself...
Always challenge me to come up with a dad joke.

