How much does a security breach cost?
How much money does a security breach cost? Looking at the IBM cost of a data breach report, I explore how information security cannot solely be a question of avoiding breaches.

"We wouldn't want our payroll information leaking and everyone to know their colleague's salaries!" This is one of the most frequent remarks I hear when discussing security with senior leadership. Here's a provocative idea: is this really the worst that could happen? How about missing payroll?
Bear with me. Let's say a spreadsheet lays around internally with this payroll information. Employees share it. Some rage quit. Uncomfortable discussions ensue. And then what? Unless the leak reveals more concerns such as a pattern of discrimination, the impact would likely remain internal.
I'm not saying it wouldn't be bad! However, such a leak would be terrible... for the members of leadership! They would need to directly deal with the crisis. For the business as a whole, the jury's still out. Do you say privacy fines? I looked at all the GDPR fines over €1,000,000. Leaks of payroll information caused none of them.
This anecdote shows the complexity of risk evaluation. We need data-driven decisions. While imperfect, sources such as IBM's Cost of a data breach report, which was released last week, can provide relevant evidence on the actual costs and impacts of security breaches.
This week, I use the report as a backdrop which I supplement with my practician's experience to answer this question: How much does a security breach cost?
But coming up with simple dollar signs would be boring. In fact, I will use this "breach cost calculation framework" to demonstrate why it is wrong to base our security messaging around breach avoidance.
This essay on breaches impacts complements my recent analysis of the 2023 Verizon Data Breach Investigation Report (DBIR), which explored the most probable causes of breaches. Since risk is a combination of probability and impact, combining both information sources will help you build more facts-based risk assessments for your organization.
IBM's 4 Costs: detection, response, notification and lost business
If somebody wants a tongue-in-cheek answer about the actual cost of a security breach, just answer them with $4.55 million USD. Mic drop. That's IBM's number! Sounds like something picked out of a hat. How is this cost broken down?
The 530 participants in the survey estimated costs in:
- Lost business (30%) such as reputation losses, diminished goodwill, outraged customers, downtime;
- Detection and escalation (30%) which encompasses investigation, forensics, crisis management, and containment;
- Post-breach response (30%) such as credit monitoring, call centers, legal fees, discounts, regulation fines;
- Notification (10%) which covers both notifications to individuals affected and to regulators.
The report also shows how these costs happen in a multi-year span. This matters. An IT director will probably stay involved only in the detection, escalation and remediation efforts. However, here I can't help but think about a CISO who's also the head of Legal or Compliance. The costs touch all their responsibilities. For them, it's an ongoing ordeal. This spread demonstrates how much organizations should think about security breaches as a business problem rather than a technology problem.
Long-time readers have probably read between the lines here: yes, this is another reason why security must stay independent from IT.
What about the market cap?
One big missing piece from the report: stock dropping following a breach. This is especially relevant, as the SEC just announced that public companies will need to report "material" breaches within 4 days of discovery, and will need to show cybersecurity literacy in their boards and senior management.
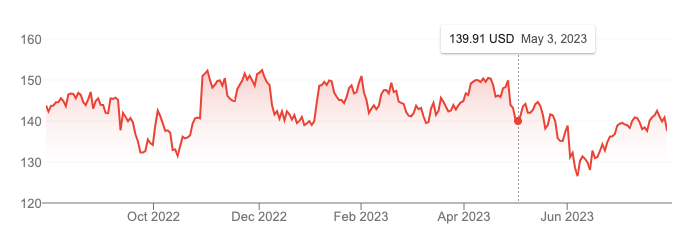
The world's biggest stock exchange authority believes security breaches matter enough to affect companies' stock values. I agree. Look at some numbers. T-Mobile has suffered over 5 security breaches in the past 5 years. Here's the stock drop following its latest mega-breach. From $150 on April 27th when the notification was sent to a little under $140 a week afterwards, we're looking at close to $12B market cap loss. Interestingly, T-Mobile has yet to recover.
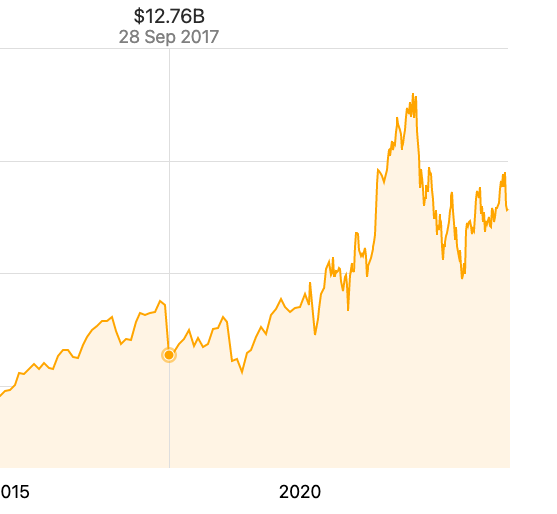
Back in 2017, credit monitoring agency Equifax showed gross negligence around its mega security breach. Its market cap toppled instantaneously. Equifax lost around 30% of its value, or $5 Billion. Executives sold their stock before the breach was announced, and ended up being convicted of insider trading. It took two years for the stock to recover.
Markets obey their own rules. I'm sure we could find companies with smaller breaches who went their way without much of a bump. That said, a major breach slashing 10%-30% on the stock seems like a reasonable assumption.
The cost of doing nothing
The biggest finding from IBM's report relates to how security investments correlate with breach savings. Essentially:
- A mature DevSecOps approach can save close to 40% on any given breach;
- Organizations that use advanced security tooling suffer 30% less costs;
- Incident Response plans and procedures can save 30%;
Now, this is great if you want to justify your cybersecurity budget. Oh and IBM has a consulting practice, wink wink. Still, the correlation does show how successful competent, and efficient employees can be.
On the flip side, here are the worst aggravating factors:
- Organizations with high-security systems complexity pay 25% more in breaches;
- Cybersecurity skills shortage also cost a 25% premium;
- Non-compliance with regulations carries a 20% difference.
All in all, technology really gets beaten up here. Be wary of cybersecurity vendors that try to spin the report into a "buy our multi-purpose platform to reduce security systems complexity". My takeaway from the report is more: stop building dashboards nobody looks at. Train security champions. Invest in your people.
Breaches are an Operating Expense
Want to make an information security specialist angry? Tell them breaches are merely an operating expense. The problem is, it's sort of true. People like me get mad because we conflate security with "the absence of breaches".
As protectors, we see breaches as a question of integrity. We won't put a dollar sign on the psychological suffering of an old woman who gets her identity stolen because some developer didn't feel like upgrading a dependency.
This is hard to write, but a report like that also helps in putting aside our emotions towards breaches. A security breach in itself is not a moral failure when a company showed due care. We can't prevent them all. As I always see: security is infinite. It doesn't end when a breach happens. Business goes on.
Where I'm getting at is: over a long enough timeline, everyone suffers a breach. We should focus more on bringing these costs down rather than measuring success in the absence of a breach.
This brings me back to one of the core questions I've been exploring on ppfosec: security leadership. Vendors use fear, uncertainty and doubt to sell security software and consulting. We, as security leaders, should rather insist on security-driven behaviours as a sign of employee proficiency. We don't collaborate on the company's incident response drills only for breach readiness. We do it because it's what drives down costs long term.

