Know What You're Up Against: Insights from the 2023 Data Breach Investigations Report
Verizon's Data Breach Investigation Report (DBIR) is a must-read resource to gain insight into current cybersecurity breaches. The 2023 version is out, and I read the whole 90 pages of it so you don't have to!

There's nothing like a story. I was drawn to information security thanks to a TV show, after all - a story. I chose to specialize in governance, risk, and compliance (GRC) over hacking because I realized this is where I could use my storytelling skills the most. A security risk assessment is merely a story: the tale of how things can go bad.
Unlike fictional stories, though, risk assessments must remain grounded in facts. My job is not to entertain. The narratives achieve our ends: advising on where to spend company resources best to protect against enemies.
This is why we need data.
The best public resource we have is Verizon's Data Breach Investigation Report (DBIR). It polls security incident data from nearly all major cybersecurity companies. The 2023 version is out, and I read the whole 90 pages of it so you don't have to!
Are you a security specialist (or an aspiring one)? Do you work in collaboration with them? Then, this summary of the state of breaches and cyber-attacks is a must-read. You will better understand how to protect your organizations!
In this edition of the newsletter dedicated to the 2023 DBIR, you will learn:
- Why do criminals hack us?
- Who are these cyber criminals?
- How do they get in?
- What is a typical security breach?
- What you should do about it.
Note: all statistics below, unless mentioned otherwise, come from the 2023 DBIR

Why do hackers attack our companies? It's all about the money
Have you watched the Netflix sensational heist series La Casa de papel? Robbers wear crazy Salvador Dali suits, wield machine guns, and fall in love with hostages. Turns out this type of violent crime has severely gone out of style. One big reason why is that it's much safer to steal online than in the "real world".
Financial motives drive 97% of security breaches. In North America, the number is 99%. Ransomware, at 24%, is still the main method to extort money. Surprisingly, the DBIR claims 93% of ransomware incidents yield no loss. As in 0$. This means all of the criminals' income comes from 7% of victims.
This motivation matters a lot. See, security textbooks train us to look at all types of motivations in our risk assessments: corporate espionage, international espionage, ideology, and grudges...
- Coming up with wild hacktivism scenarios means you are attracting the attention of your executives towards 1% of the problem.
- Espionage is overrepresented in security textbooks. According to the data, all of the espionage threats are in the public sector.
Interestingly, it appears the FBI's efforts to crack down on the REvil group that targeted hospitals and government agencies bore fruit. Cybercriminal gangs have stirred away from these targets in favour of private for-profit businesses.
Your enemy wants money from you. And yes, they are cybercriminals above all.

Who are the attackers? It's very simple to answer!
I will never forget the first big security conference I attended. There was this keynote from a huge security vendor's VP of whatever where for 55 minutes he couldn't shut up about nation-state attacks and how their technology could thwart these within minutes.
It's somewhat sexy to imagine China and Russia unleashing their whole hacking army on your business. It's also a marginal phenomenon. Here's the breakdown:
- Organized crime groups orchestrated over 70% of breaches;
- Misconfiguration from internal users, 15%;
- State-sponsored threat actors count for less than 10% of attackers;
- 4% of breaches originate from disgruntled employees
The DBIR also provides some insight into criminal gangs' mode of operations. Many groups work by vertical, with financial services being the clear #1 target. Retail and eCommerce also face a slew of credit card attacks, which makes the good old PCI-DSS standard still relevant, to the dismay of many.
Once again, I feel the data contradicts the security textbooks. Your organizations should start investing in wild "insider breach" and "Advanced persistent threats (APT)" scenarios only when it has nailed down organized cybercriminals groups.
My theory about what's happening is many cybersecurity specialists experience a version of the "spotlight effect":
The spotlight effect is the psychological phenomenon by which people tend to believe they are being noticed more than they really are.
So alright, we know criminals target us for financial purposes. But how do they get in?

How do they infiltrate our systems?
Hacker friends, I know cross-side scripting, time-of-check-time-of-use and buffer overflows are cool. They're just way, way behind password attacks when it comes to "how hackers break in". Look at the numbers:
- The principal entry point are web-facing servers and applications, such as email servers, security software, and cloud apps.
- 86% of attacks against such web-facing assets involve credential attacks (password reuse, password guessing, password theft, etc.)
- Only 10% of attacks against public servers involve the exploitation of a vulnerability;
- 49% of all attacks involve credentials, which increases to 67% in North America;
The most impressive statistic comes from the surge in business email compromise and pretexting. These practices show criminals' increased savviness and patience. When they gain access to an email inbox, criminals will quietly insert themselves into email threads to stir conversation toward fraudulent activities. As Microsoft put it, business email compromise is up 38%.
Think about it. If a hacker compromises the Head of Finance's laptop, how long before the Security Defense team picks it up? With a good EDR, hackers will not be able to install any exploitation tool... But imagine simply approving a fake purchase order for a fake product that you control. I'm not making this up with my imagination! This is the real world, right now.
The Anatomy of a Typical Breach: Putting it all together
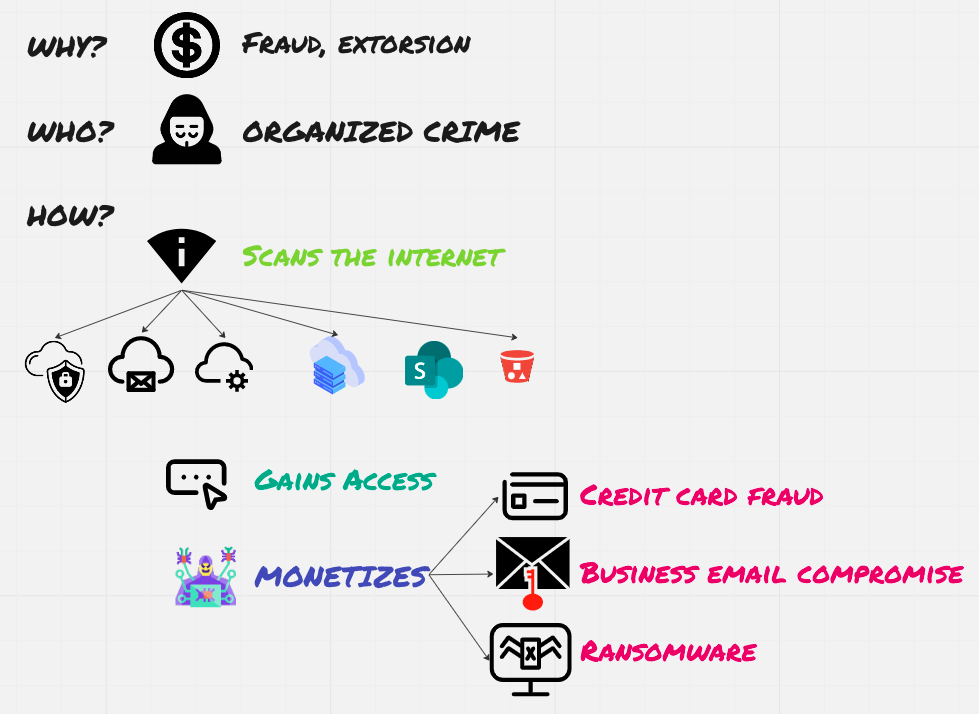
A typical breach in 2023 looks like this:
- Organized crime group looks to make financial gains;
- To find a target, they scan the internet for exposed services, or they go with companies in their vertical;
- To gain access, they conduct various password attacks or use exploits purchased from other groups or on forums;
- Monetization is stealthy, multi-faceted, and coordinated.
This is the dominant narrative for most organizations these days.

Now, what should you do to prevent data breaches?
Today's security breaches are therefore opportunistic. Cybercriminal gangs also operate in a business-like manner: targets that are too complex do not justify the return on time investment, they will move to something else cheaper and easier to compromise.
To not become the low-hanging fruit, the basics must apply:
- An access controls architecture that enforces a significant amount of separation between systems;
- Mandatory phishing-resistant multi-factor authentication (MFA) such as FIDO keys;
- A password manager that generates 99-characters-long passwords or, even better, a Privileged access management (PAM) solution.
Over-reliance on email appears as an immense challenge. The problem likely worsened with the increase in remote work. Businesses should strive to stray away from emails in their business processes.
Finally, I believe our profession warrants a bit of humility. In most cases, we're not as important as we think: money is probably not best spent on fancy espionage, state-sponsored, hacktivist, or disgruntled employee scenarios.
🥊 Other cool stats from the 2023 DBIR
- In the crypto industry, 50% of breaches come from web application flaws, whereas email attacks account for only 10%. This suggests a level of immaturity in the frameworks developers use in this area.
- Denial of Service (DoS) accounts for 40% of "incidents". The DBIR does not count a DoS as a "breach", per see. This demonstrates the persistent popularity of botnets, as I wrote in Can IoT Devices be Hacked?.
- Stolen credentials caused 77% of breaches in the financial sector. Companies would prefer to disclose they faced a "highly sophisticated attack" from "nation-states", but in reality, it's a simple password being "Qwerty1234!"...

