Exclusive: Security Absent from Twitter Terms

I reviewed Twitter's public documentation and security is absent
In August 2022, the former Twitter Chief Information Security Officer made incendiary allegations against Twitter. I decided I would go through Twitter's publicly available contracts to determine the gap between the allegations and the requirements Twitter committed itself to uphold.
Terms of Service
I began with the Terms of Service, which looked standard for a Business to Consumer (B2C) model. The beauty of B2C for Twitter is that nobody actually reads these, except maniacs like me that do it so you don't have to.
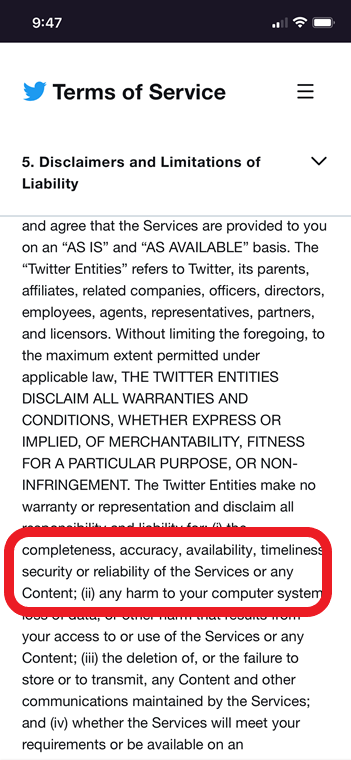
Its two main elements are part of the Limitation of Liability (LoL - no, really, that's what lawyers call it: the LOL): products are provided "as-is" at "our own risk" and there are no guarantees on the security of the service (see highlighted below). The second part of the LoL, in all capitals like somebody yelling in MSN Messenger so you know they mean business, restricts damages to $100 USD in case of a lawsuit. In other words: if Twitter gets hacked, they expect users to settle for $100 USD in a class action lawsuit. This is actually a pretty good deal considering Canadian restaurant chain Tim Horton's got away with "free coffee and donuts" for unauthorized geolocation data collection.

DPA
Things were pretty bare in the ToS security-wise so I went a bit out of the box and found Twitter's standard Global Data Processing Addendum (DPA) for its partners. A DPA is basically the "GDPR contract" where companies agree on how personal data will be shared between them and their respective responsibilities towards privacy rights: who gathers consent, who enforces the right to be forgotten, the right to accessibility, foreign data transfers, and... "technical and organizational measures" a.k.a Security. Technical and organizational measures (I call them TOMs) are basically GDPR Article 32 copy-pasted. When a company feeds you Article 32 verbatim in a DPA it is usually what I call, pardon my French, compliance bullshit. And this is what Twitter has in its DPA (see below). The funny thing is that Twitter refers to "Your Agreements", which I could not find a copy of!
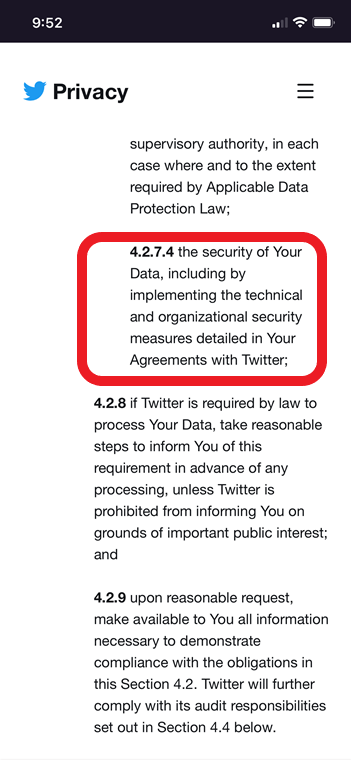
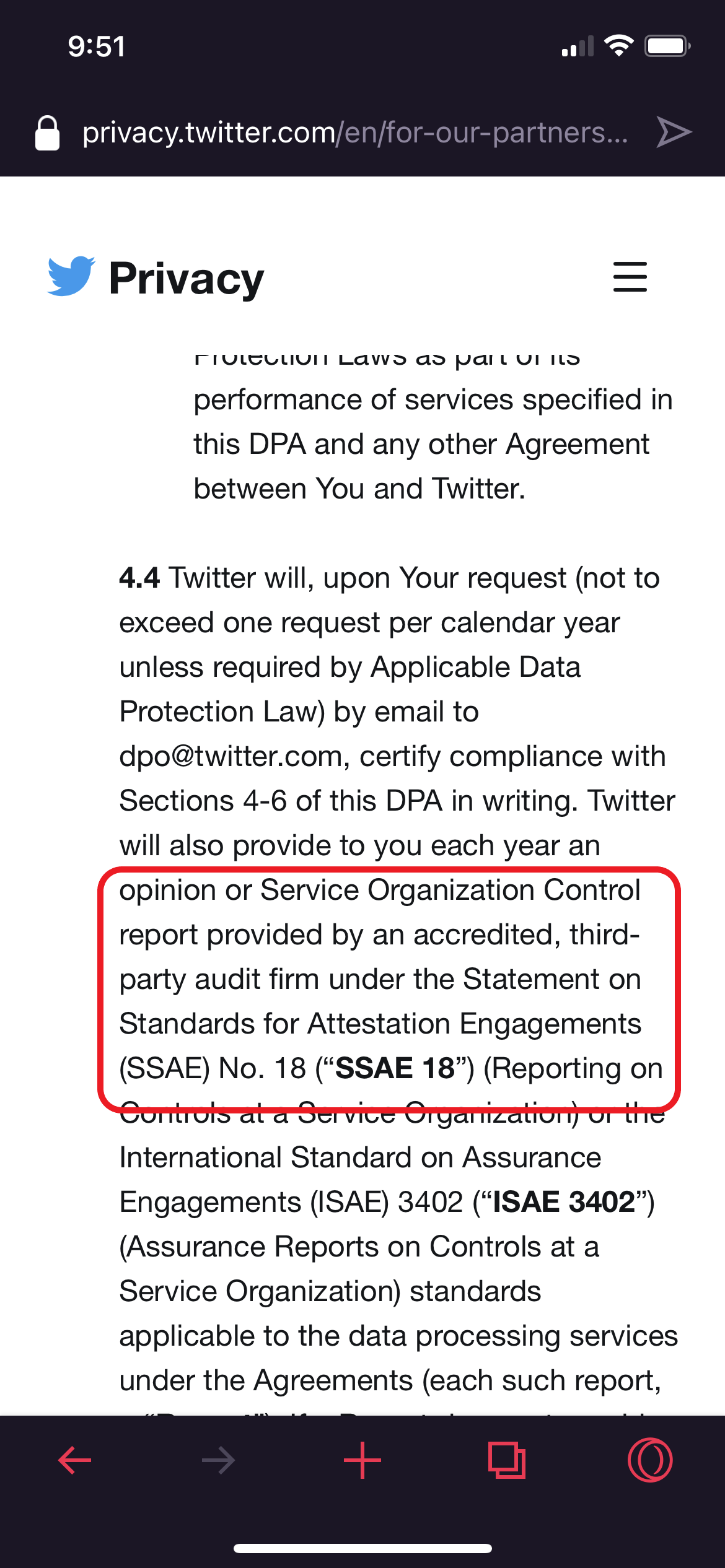
The only mention of security is highlighted in the second image, where Twitter confirms it maintains a SOC report. This in my opinion does change a lot with regards to the allegations against Twitter! A state-of-the-art SOC2 audit would ask for samples of servers and workstations to see whether they are adequately patched and encrypted. The beauty of such audits is that, by design, they generate a TON of evidence and trails: that's the whole point of the exercise! The audit artifacts would immediately reveal either:
- the whistleblower lied,
- or Twitter representatives lied to the auditor,
- or the auditor was complacent/complicit.
Who said SOC2 was useless?
Contracts stopped there, although I kept searching for any written public commitment from Twitter.
Twitter Blog
I was able to find four blog posts about Twitter's platform security: from 2017 (GDPR prep), 2019 (indirectly addresses security through "technical debt"), 2020 (as a response to an incident), and 2021 (which coincide with the whistleblower's report of the board seeing a "whitewashed" report on security). The 2021 blog post has this especially chilling bullet point: "Providing annual reports from our CISO and CPO to our full Board of Directors to drive awareness, alignment and accountability on privacy and security." Amongst these posts, only the 2020 one illustrates Twitter's platform's tangible security measures. All in all, we can all agree that a corporate marketing blog does not make a security program.
Security in the Help Centre
The Support centre Security section solely focuses on Twitter's security features which allow Twitter users to protect their accounts. There is no mention of Twitter's backend or organizational processes.
The Developers Portal
Twitter's API documentation has a security section as well, which almost entirely tells developers how to secure their applications. On the other hand, Twitter's bug bounty program has no red flags, with an impressive $1.5 million paid to security researchers.
Remaining Questions
I feel shocked by Twitter's silence on security considering how good their Privacy approach is. I used their Privacy Policy in the past as an example of how it should be written with an educational, no lawyer-ish way to address the reader. Since privacy and security go hand in hand (can't have privacy without security), the latter's absence is glaring.
I am not a conspiracy theorist and I believe in Hanlon's razor: "never attribute to malice that which is adequately explained by stupidity". I do not believe Twitter's legal deliberately obfuscated security to hide the weaknesses Peiter Zakto points out. I think both teams were working in silos and security never made it to these areas because that's what happens in most organizations!
In conclusion, based on the publicly available information, I cannot assess how secure the Twitter platform really is or could be. As a B2C, Twitter does not have a sufficient incentive to be transparent. Compare Twitter's silence with Salesforce, one of the world's biggest B2B platforms, 27-page security eBook!
When market pressure is not enough, regulators must step in. Twitter is one of the world's leading platforms. It is critical to share ideas and knowledge. Peiter Zatko is right when he claims Twitter's security deficiencies are a threat to democracy and national security. Its owners have a duty to protect their users, whether they intended the platform to become so critical or not. Now the question remains: who, in the information security field, will want to work for them?

