Why Are So Many Companies Getting Hacked?
How and why do you seem to be experiencing every week some type of cybersecurity event in your digital life, and what to do about it?

I got a weird credit card transaction notification during my son's birthday party a few weeks ago. I looked up the records and filed a report. It took about 10 minutes, but I remained distracted by the incident for an hour. Nobody noticed. I simply felt bad about being out of the moment for a while, which kind of snowballed into "feeling bad about feeling bad" territory.
I think this event illustrates what I call "death by a thousand cuts" (no relation to the Taylor Swift song) we go through in modern life. Little irritants that in themselves are no big deal, but that end up piling up until you can't take it anymore.

Cybersecurity incidents are part of these paper cuts. Your password manager gets hacked and you must rotate 25 passwords from your vault. The week after it's your favourite website that goes down for a week. You get text messages from spammers pretending to be the Revenue Agency or the CEO of your employer. Annoyances build up on top of the "real" stuff: a relative's deteriorating health, quitting on your habits, conflicts with your friends, your dog's weird noises...
Companies know how much security breaches annoy their customers. It gives them bad press. Their marketing strategy gets flushed down in seconds. So why do these keep happening, why there seems to be more? Haven't we learned? Are the hackers that powerful?
This week, we'll look at how and why you seem to be experiencing every week some type of cybersecurity event in your digital life, and what to do about it. I'll look at:
- How your run-of-the-mill cybercriminals pick their victims and make money,
- Why do organizations with immense resources such as governments, banks, hospitals, and big tech companies keep getting hacked,
- Actions to reduce breaches' impacts
Don't Be The Low Hanging Fruit

I felt compelled to write about cybersecurity breaches this week because Indigo, Canada's largest bookstore, has been shut down for ten days and counting after an incident. Technical details are scarce, but the attack has all the hallmarks of ransomware. Why would hackers target Indigo? Why not?
Hackers are lazy, just like us! They will gladly pick low-hanging fruits to make a buck. What do I mean by a "low-hanging fruit"? The breakdown of the hack that lead to the TSA "no-fly list" being leaked tells you everything about the mindset. Hackers use websites such as shodan.io to find "internet-facing" computers. All kinds of services can be left "wide open" to the public:
- a remote desktop service to allow IT professionals to manage servers from their homes,
- a multimedia server such as Plex that people use to watch films remotely from their home computer,
- a multiplayer game you host with your friends,
- an enterprise developer tool, such as Jenkins
Once threat actors find these easy pickings, all they need to do is password attacks. To avoid getting locked out, the simplest way to attack is "password spraying": you take the most used passwords "dictionaries", which are available with a simple Google search, and try them on every user you can associate with the domain of the exposed machine. And voilà.
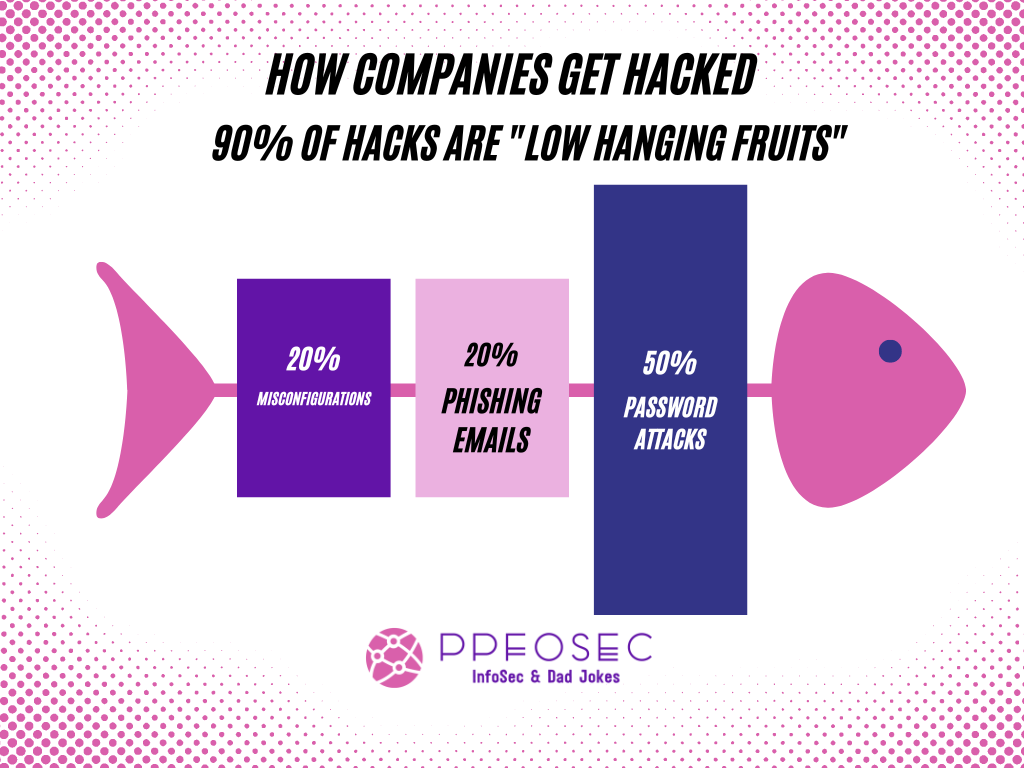
Most security breaches you see in the news are simple:
- Compromised passwords like the ones I described, can make up to 50% of attacks, according to research.
- Phishing e-mails, where users will be invited to input their passwords in a fake online form, or prompted to install malware on their devices, constitute another 20%.
- Another 20% comes from "human errors", typically cloud storage that is accidentally made "public", like the US military who leaked 3 TB worth of unclassified emails.
Even amongst the remaining 10%, the hacks do not look anything like Hollywood-type heists. Remote injection of malware leverages well-known exploits such as ProxyShell or log4shell, which are accessible to beginners. This is not a skills game in these scenarios. This is all about patience and the will to commit a crime.
Still, there are sharks out there as well...
Anybody Can Be Breached Given Enough Time

Enterprises that can afford full-time security staff have fixed these low-hanging fruits. Yet, why are they getting hacked as well? How can GoDaddy, a web hosting giant, be a victim of a multi-year breach? How can LastPass, a password security company, suffer the same fate? Try long enough, you'll get lucky.
Looking at it on a broad scale, let's say hackers go from phishing to spear phishing. Highly skilled hackers join criminal organizations, such as the Lapsus$ or 0kta group, which targets industries, such as gaming or high tech. If one looks at how Reddit was hacked, the wrongdoers cloned the company's intranet. After, they built a fake portal that sent them the one-time multi-factor authentication. Not trivial!
Most of the attacks against tech companies attempt to use this vendor as a jump point into their customers' networks, where the true potential for damage (and thus ransom) resides. The most vicious groups, such as Hive, which was dismantled by the FBI in February 2023, paralyzed critical infrastructure such as power, transport, and even healthcare. All for a ransom.
The silver lining? These sophisticated attacks are less and less lucrative due to companies' preparedness and recovery strategies. Unfortunately, this is a perpetual arms race. Security is an infinite game. This is why what we need, in the long run, is psychological resilience.
What About Me? How Can I Prepare?

No, this is not the part where I tell you to use strong authentication and be careful with suspicious emails. That's for another post. Plus, you can have the best cyber hygiene, and it won't prevent your school from being hit by ransomware. I'm looking at the problem from a mental preparedness perspective.
When I began Jiu-Jitsu training, I spent months learning how to fall. What do we keep thinking about avoiding hits, when falling is part of the fight?
This is how I want to talk to you about security breaches. Many infosec experts you will meet don't get this. It's not about avoiding them (the breaches, not the experts), because, in the end, we are powerless. On a personal level, it's about managing how deep the cuts will be, so you can take one thousand and one cuts, and two, and three...
My "expert" advice? Make a "map" of your most important accounts. Don't pressure yourself to get them all. Look at which apps are on your phone's home screen. See who's emailing you often. This will give you an idea! All security starts with knowing what is valuable and choosing what you must protect. You have limited time and willpower. Everybody is like that. So pick the most important ones and make a contingency plan.
I was lucky in a sense to get that unusual credit card transaction: within minutes I could file an issue using the company's mobile app. You won't be so lucky if somebody files your taxes for you.
There's no way to know who's going to get got. You can't research every website you share your information with, every service provider, and every institution... At a certain moment, you are gambling with your information, just like everybody else. The most important thing is your mental state. I can't find the source, but as former mixed martial arts champion George St-Pierre once said about punches to the face: "It's the ones you don't see that hurt".
That doesn't mean we must surrender! Organizations that care are less likely to get breached, and if they do, they will act transparently and diligently to minimize the impacts. Those who don't care must be held accountable for their shortcomings, especially by cyber insurance companies. When the market cannot set sufficient quality and security standards, regulation must step in as well.
I get asked why I'm on TikTok. Every week there is a tirade on LinkedIn shaming people for getting sucked into the silly-video-zapping machine run by the Chinese government. "Don't you care about your privacy?" I do. Privacy, after all, is about informed consent. Whatever I share with that platform, I know what I'm getting into. Paragliders know full well the dangers, and so do climbers. Why should it be different for online habits? What matters is knowledge and awareness.
I hope this is what you got out of all this.

